Thursday, 29 April 2010
Halo is one of my favorite games and I still duke with my friends in weekend LAN mayhem, the same can be said about 
"Today we are very proud to announce a ground breaking ten year partnership between Bungie, one of the greatest developers in the world and the makers of Halo, with Activision, the number one video game publisher, who will bring the new intellectual property to fans worldwide across all platforms"In short, the equation goes like this -

The deal took over an year to finally come to a mutual point of interest, and personally, I can see some real Bungie stuff of Oni quality to be developed outside halo universe.
Meanwhile Bungie is currently preparing itself for Halo: Reach for Xbox 360,self dubbed as the "most ambitious game" it has ever made. Mean while you can enjoy the Halo Reach trailer :)
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Thursday, 29 April 2010 by Lucky · 0
Wednesday, 28 April 2010
Its a digital nightmare when your password gets hacked. Password compromise = your are fucked, straight away. 
About Bad Passwords
Poor weak passwords have the following characteristics (if you have even one,make sure to change it) -
- Password size less than 15 characters
- Password is a word from dictionary
The password is -
- Name of family,pet,your favorite videogame character.
- Computer terms,commands,website name,hardware,software etc.
- Personal data like birthday,mobile phone numbers, address etc.
- Any of the above spelled backwards! or succeeded or preceded by a number or letter (password1, 1 password)
- In short any form of personal stupidity leads to tragic events :P
How to get hacked ?
- Reveal your password to any one.
- Reveal it in an email message,phone call,to your boss, give hints to others,share it with friends and co workers.
- Write it down somewhere.
- Keep same passwords for all your digital ventures, like emails, voicemails etc
- NEVER CHANGE IT.

In any case, if you want the opposite, follow the opposite :)
Making a STRONG Password
use phrases to form passwords, these are much secure to form and hard to guess.
for eg, the phrase -
“ This is a super secure password and is hard to hack :P ”
will form a password given below by taking the first letter and substituting similar sounding words with numbers. See..its quite hard to hack :)
“ Tiassp&ih2h:P ”
Use numbers, letters, uppercase and lowercase and mix them freely to form you password. make sure its not a dictionary word and DOES NOT CONTAIN any characteristic of weak passwords stated earlier.
A more secure version is to use passphrases to form passwords. A passphrase is a longer version of password and hence its more secure. Make sure its easy to remember,not a famous quotation and hard to guess by intuition
As Clifford Stoll says,
“ Treat your password like your toothbrush. Don't let anybody else use it, and get a new one every six months “
He is damn right..just make sure you change it every month or more often to be secure.
I guess you will now be able to form secure passwords and deploy them fully.
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Wednesday, 28 April 2010 by Lucky · 0
Tuesday, 27 April 2010
Too much new software is vulnerable to the attack sequences of yesteryear. This suggests a testing approach: a comprehensive set of known attack pattern sequences can be leveraged for use in targeted fuzzing when testing for exploitable conditions in new applications.Fuzzdb is a comprehensive set of known attack pattern sequences, predictable locations, and error messages for intelligent brute force testing and exploit condition identification of web applications.
Many mechanisms of attack used to exploit different web server platforms and applications are triggered by particular meta-characters that are observed in more than one product security advisory. fuzzdb is a database attack patterns known to have caused exploit conditions in the past, categorized by attack type, platform, and application.
Because of the popularity of a small number of server types, platforms, and package formats, resources such as logfiles and administrative directories are typically located in a small number of predictable locations. A comprehensive database of these, sorted by platform type, makes brute force fuzz testing a scalpel-like approach.
Since system errors contain predictable strings, fuzzdb contains lists of error messages to be pattern matched against server output in order to aid detection software security defects.
Primary sources used for attack pattern research:
- researching old web exploits for repeatable attack strings
- scraping scanner patterns from http logs
- various books, articles, blog posts, mailing list threads
- patterns gleaned from other open source fuzzers and pentest tools
- analysis of default app installs
- system and application documentation
- error messages
It’s like a non-automated open source scanner without the scanner. You can download fuzzdb v1.06 here:
Check out via svn: svn checkout
http://fuzzdb.googlecode.com/svn/trunk/ fuzzdb-read-only
Also..to keep FuzzDB updated,type
svn update
to pull the latest updates.
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Tuesday, 27 April 2010 by Lucky · 0
Sunday, 25 April 2010
A blogger who goes by the name of “Protocol snow” has been banned by Apple for buying iPads.The story goes like this, as Apple launched iPads and people went crazy for it, there was a shortage of iPads all over the world. Since Mr Snow was lucky enough to live near an Apple store which had plenty of iPads available, and “coincidently” was a member of NeoGaf gaming forums, he ordered iPads and decided to sell and ship them to his fellow NeoGAFians by covering all the shipping costs,tax,Paypal insurance fees along with the iPad. The prices were quite reasonable and he limited his purchases to no more than 2 per day because he heard that there was a limit per person.
Then he went shit out of luck on April 17, when Mr Snow’s fateful visit at Apple store limited his purchases to an end for the rest for his life. The unexpected conversation between Mr Snow (Me) and Apple folks (Guy#1, Guy#2),that concluded his ban went like this -
Me (nonchalantly) — “Is there an issue?”Guy #2 — “There is a limit to the number of iPads that customers can buy.”Me (playing dumb) — “Oh, is that right? What’s the limit?”Guy #2 — “Only 2 per customer.”Guy #1 — “I’m sorry sir, but you have reached your lifetime limit of iPad purchases and will not be allowed to buy any more.”Me (anticipating that statement) — “Is the iPad limit per person? Per credit card? Per household?”Guy #1 — “All I can say is that you have reached your lifetime limit.”Me — “What does that mean? Can I use a different credit card to buy it? I’m buying this for a friend.”Guy #1 — “You are not allowed to buy this iPad.”Me — “Uhh… is it ok if I have a family member or friend come to buy it for me? My reservation doesn’t expire until 6:00 PM.”Guy #1 — “All I can say is that you have reached your lifetime limit.”Me (suddenly realizing what he’s saying) — “Wait, what? Lifetime? What does that mean?”Guy #1 — “All I can say is that you have reached your lifetime limit of iPads and will not be allowed to buy any more.”Me — “I’m banned from buying iPads? I know there’s a shortage right now, but I can’t buy any more once there’s plenty of stock?”Guy #1 — “All I can say is that you have reached your lifetime limit.”Me — “Ok buddy, I’m not going to make a scene so I’m leaving. How many iPads is the limit by the way?”Guy #1 — “That information is not available.”Me (looking at Guy #2, who has been silent this whole time) — “He tells me that the limit is two.”Guy #1 — “I wish I could say but I do not have that information.”Me — “I’ve already purchased more than 2 iPads. Why didn’t anybody else stop me in the past?”Guy #1 — “I wish I could say but I do not have that information.”Me — “Alright, I’ve had enough. Have a good day.”
Posted by XERO. ALL RIGHTS RESERVED.
Sunday, 25 April 2010 by Lucky · 0
Thursday, 22 April 2010

While I am not messing up with my pc, watching AVGN, or reading wikipedia, I prefer to be at Attrition.Org which in my opinion is the best place to hangout after any LUG. For those who don't know about Attrition.Org, its basically a “hobby site” that focuses on computer security and mocks the revered security researchers who are basically frauds with illiterate whoring media on their side.
As the description on the site says -
Attrition.org (http://attrition.org/ ) is a computer security web site dedicated to the collection, dissemination and distribution of information about the security industry for anyone interested in the subject. They maintain one of the only open and honest grim look at the industry, reminding everyone that we must strive to be better than we have been historically. Their crusade to expose industry frauds and inform the public about incorrect information in computer security articles is a primary goal of the site.
My favorite section is the charlatans section of the website, where fake security experts are bashed for their fraudulent actions and other “unethical” reasons. My favorite one is the case of Ankit Fadia, the once acclaimed Indian child prodigy and author(though in my opinion, nothing more than a script kiddie, lots of poor journalism is responsible for getting him the place he stands today).
Additionally, Attrition regularly publishes opinion pieces such as "Security Rants" pointing out problems with the computer security industry.Folks at Attrition are responsible for maintaining one of the biggest list of defaced websites (though they ceased to maintain it after 2001) and maintained Data loss database which records the data breaches at companies.
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Thursday, 22 April 2010 by Lucky · 0
Tuesday, 20 April 2010
At Captivate 2010, fighting crossover giant Capcom has announced what fans have been wanting form a long time – Marvel vs Capcom 3. For those who don't know what it is all about, its the series that defined crossover fighting games and is the fifth installment in its series. As usual, the game will feature a whole array of Marvel and Capcom characters including fan favorites Ryu, Morrigan from Capcom fighting roster and Wolverine,Hulk,IronMan from Marvel’s side. The best part? Chris Redfield is included in the upcoming installment and trust me, its going to be awsummmm !!!! MVC3 is the first to feature 3D graphics in its series and like its predecessor, will be featuring a 3-on-3 tag-team based fighting system. The game will be powered by Capcom’s MT framework engine which has previously illustrated its prowess in Resident Evil 5, Devil may Cry 4 and Lost Planet.

On a personal note, I prefer Street Fighter more..but I m a fighting game junkie and I still remember duking out with my friends in Marvel vs Capcom 2 and the whole experience wants some more bashing :)
MVC3 will be released on PS3 and Xbox 360..Who knows it might also be released on PC too, as its powered by MT framework and we already have Street Fighter 4 with us.
You can check out the cool trailer below :)
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Tuesday, 20 April 2010 by Lucky · 0
Monday, 19 April 2010
 Step 1 : Open a New 640 x 400 pixel document by going to File>New.
Step 1 : Open a New 640 x 400 pixel document by going to File>New.































Monday, 19 April 2010 by Lucky · 0
Friday, 16 April 2010
As I was checking several blogs and websites today, i found that several of them redirected me to either gescansecurity.org or a bing search page for “freevirusscan” .
Several blogger and wordpress blogs were seemed to have been affected. In my case I visited this blog (gosh..its a blogger blog) and this site was redirected to -
which first displayed a window almost identical to a standard "My computer" screen on a windows pc and looked like the typical type of windows malware. It alerted me of various viruses/Trojans (downloader.win32.agent etc.) detected on my computer, followed by a prompt to install "System Security Antivirus" and such by clicking "ok". With no option to close the window, and with no other active windows, I clicked cancel for no result as I got a message that windows security center recommends it as an install and hence the cycle repeats.
When I got rid of that page and revisited it,the page was gone and instead redirected me to a bing search page for search term “freevirusscan” .
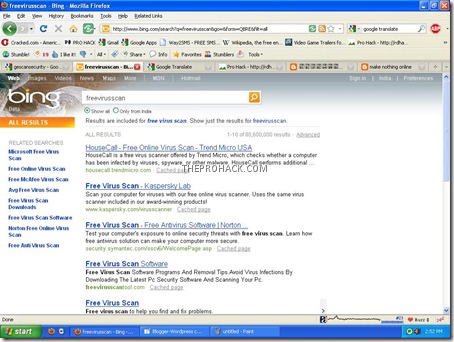
On closer inspection I found out that affected blogs load a script just before the </body> tag with no recognizable pattern (atleast for me). Also I monitored my cookies and found that after being redirected to bing,a cookie is set to prevent the user from being redirected for 20 days.
Several wordpress blogs also displayed the same vulnerability. On later googling I found a user in apple forum about the same problem. A new virus attack on Wordpress/Blogger ? Seems so as I was running Linux and seemed to have no malware installed on my Linux machine. Tested this on a clean windows machine and for positive results.
Keep your eyes open folks..
Like This post ? You can buy me a coffee :)
Posted by XERO. ALL RIGHTS RESERVED.
Friday, 16 April 2010 by Lucky · 0
Thursday, 15 April 2010
“Fatal error: the system has become unstable or is busy," it says. "Enter to return to Windows or press Control-Alt-Delete to restart your computer. If you do this you will lose any unsaved information in all open applications."
You have just been struck by the Blue Screen of Death.

Anyone who uses Microsoft Windows will be familiar with this. What can you do? More importantly, how can you prevent it happening?
Lets get down on it…
Hardware conflict
The number one reason why Windows crashes is hardware conflict. Each hardware device communicates to other devices through an interrupt request channel (IRQ). These are supposed to be unique for each device.
For example, a printer usually connects internally on IRQ 7. The keyboard usually uses IRQ 1 and the floppy disk drive IRQ 6. Each device will try to hog a single IRQ for itself.
If there are a lot of devices, or if they are not installed properly, two of them may end up sharing the same IRQ number. When the user tries to use both devices at the same time, a crash can happen. The way to check if your computer has a hardware conflict is through the following route:
* Start-Settings-Control Panel-System-Device Manager.Often if a device has a problem a yellow '!' appears next to its description in the Device Manager. Highlight Computer (in the Device Manager) and press Properties to see the IRQ numbers used by your computer. If the IRQ number appears twice, two devices may be using it.
Sometimes a device might share an IRQ with something described as 'IRQ holder for PCI steering'. This can be ignored. The best way to fix this problem is to remove the problem device and reinstall it.
Sometimes you may have to find more recent drivers on the internet to make the device function properly. A good resource is www.driverguide.com. If the device is a soundcard, or a modem, it can often be fixed by moving it to a different slot on the motherboard (be careful about opening your computer, as you may void the warranty).
When working inside a computer you should switch it off, unplug the mains lead and touch an unpainted metal surface to discharge any static electricity.
To be fair to Microsoft, the problem with IRQ numbers is not of its making. It is a legacy problem going back to the first PC designs using the IBM 8086 chip. Initially there were only eight IRQs. Today there are 16 IRQs in a PC. It is easy to run out of them. There are plans to increase the number of IRQs in future designs.
Bad Ram
Ram (random-access memory) problems might bring on the blue screen of death with a message saying Fatal Exception Error. A fatal error indicates a serious hardware problem. Sometimes it may mean a part is damaged and will need replacing.
But a fatal error caused by Ram might be caused by a mismatch of chips. For example, mixing 70-nanosecond (70ns) Ram with 60ns Ram will usually force the computer to run all the Ram at the slower speed. This will often crash the machine if the Ram is overworked.
One way around this problem is to enter the BIOS settings and increase the wait state of the Ram. This can make it more stable. Another way to troubleshoot a suspected Ram problem is to rearrange the Ram chips on the motherboard, or take some of them out. Then try to repeat the circumstances that caused the crash. When handling Ram try not to touch the gold connections, as they can be easily damaged.
Parity error messages also refer to Ram. Modern Ram chips are either parity (ECC) or non parity (non-ECC). It is best not to mix the two types, as this can be a cause of trouble.
EMM386 error messages refer to memory problems but may not be connected to bad Ram. This may be due to free memory problems often linked to old Dos-based programs.
BIOS settings
Every motherboard is supplied with a range of chipset settings that are decided in the factory. A common way to access these settings is to press the F2 or delete button during the first few seconds of a boot-up.
Once inside the BIOS, great care should be taken. It is a good idea to write down on a piece of paper all the settings that appear on the screen. That way, if you change something and the computer becomes more unstable, you will know what settings to revert to.
A common BIOS error concerns the CAS latency. This refers to the Ram. Older EDO (extended data out) Ram has a CAS latency of 3. Newer SDRam has a CAS latency of 2. Setting the wrong figure can cause the Ram to lock up and freeze the computer's display.
Microsoft Windows is better at allocating IRQ numbers than any BIOS. If possible set the IRQ numbers to Auto in the BIOS. This will allow Windows to allocate the IRQ numbers (make sure the BIOS setting for Plug and Play OS is switched to 'yes' to allow Windows to do this.).
Hard disk drives
After a few weeks, the information on a hard disk drive starts to become piecemeal or fragmented. It is a good idea to defragment the hard disk every week or so, to prevent the disk from causing a screen freeze. Go to
* Start-Programs-Accessories-System Tools-Disk DefragmenterThis will start the procedure. You will be unable to write data to the hard drive (to save it) while the disk is defragmenting, so it is a good idea to schedule the procedure for a period of inactivity using the Task Scheduler.
The Task Scheduler should be one of the small icons on the bottom right of the Windows opening page (the desktop).
Some lockups and screen freezes caused by hard disk problems can be solved by reducing the read-ahead optimisation. This can be adjusted by going to
* Start-Settings-Control Panel-System Icon-Performance-File System-Hard Disk.Hard disks will slow down and crash if they are too full. Do some housekeeping on your hard drive every few months and free some space on it. Open the Windows folder on the C drive and find the Temporary Internet Files folder. Deleting the contents (not the folder) can free a lot of space.
Empty the Recycle Bin every week to free more space. Hard disk drives should be scanned every week for errors or bad sectors. Go to
* Start-Programs-Accessories-System Tools-ScanDiskOtherwise assign the Task Scheduler to perform this operation at night when the computer is not in use.
Fatal OE exceptions and VXD errors
Fatal OE exception errors and VXD errors are often caused by video card problems.These can often be resolved easily by reducing the resolution of the video display. Go to
* Start-Settings-Control Panel-Display-SettingsHere you should slide the screen area bar to the left. Take a look at the color settings on the left of that window. For most desktops, high color 16-bit depth is adequate.
If the screen freezes or you experience system lockups it might be due to the video card. Make sure it does not have a hardware conflict. Go to
* Start-Settings-Control Panel-System-Device ManagerHere, select the + beside Display Adapter. A line of text describing your video card should appear. Select it (make it blue) and press properties. Then select Resources and select each line in the window. Look for a message that says No Conflicts.
If you have video card hardware conflict, you will see it here. Be careful at this point and make a note of everything you do in case you make things worse.
The way to resolve a hardware conflict is to uncheck the Use Automatic Settings box and hit the Change Settings button. You are searching for a setting that will display a No Conflicts message.
Another useful way to resolve video problems is to go to
* Start-Settings-Control Panel-System-Performance-GraphicsHere you should move the Hardware Acceleration slider to the left. As ever, the most common cause of problems relating to graphics cards is old or faulty drivers (a driver is a small piece of software used by a computer to communicate with a device).
Look up your video card's manufacturer on the internet and search for the most recent drivers for it.
Viruses
Often the first sign of a virus infection is instability. Some viruses erase the boot sector of a hard drive, making it impossible to start. This is why it is a good idea to create a Windows start-up disk. Go to
* Start-Settings-Control Panel-Add/Remove ProgramsHere, look for the Start Up Disk tab. Virus protection requires constant vigilance.
A virus scanner requires a list of virus signatures in order to be able to identify viruses. These signatures are stored in a DAT file. DAT files should be updated weekly from the website of your antivirus software manufacturer.
An excellent antivirus program is McAfee Virus Scan by Network Associates ( www.nai.com). Another is Norton Antivirus 2000, made by Symantec ( www.symantec.com).
Printers
The action of sending a document to print creates a bigger file, often called a postscript file.
Printers have only a small amount of memory, called a buffer. This can be easily overloaded. Printing a document also uses a considerable amount of CPU power. This will also slow down the computer's performance.
If the printer is trying to print unusual characters, these might not be recognized, and can crash the computer. Sometimes printers will not recover from a crash because of confusion in the buffer. A good way to clear the buffer is to unplug the printer for ten seconds. Booting up from a powerless state, also called a cold boot, will restore the printer's default settings and you may be able to carry on.
Software
A common cause of computer crash is faulty or badly-installed software. Often the problem can be cured by uninstalling the software and then reinstalling it. Use Norton Uninstall or Uninstall Shield to remove an application from your system properly. This will also remove references to the program in the System Registry and leaves the way clear for a completely fresh copy.
The System Registry can be corrupted by old references to obsolete software that you thought was uninstalled. Use Registry Cleaner to clean up the System Registry and remove obsolete entries.
Often a Windows problem can be resolved by entering Safe Mode. This can be done during start-up. When you see the message "Starting Windows" press F4. This should take you into Safe Mode.
Safe Mode loads a minimum of drivers. It allows you to find and fix problems that prevent Windows from loading properly.
Sometimes installing Windows is difficult because of unsuitable BIOS settings. If you keep getting SUWIN error messages (Windows setup) during the Windows installation, then try entering the BIOS and disabling the CPU internal cache. Try to disable the Level 2 (L2) cache if that doesn't work.
Remember to restore all the BIOS settings back to their former settings following installation.
Overheating
Central processing units (CPUs) are usually equipped with fans to keep them cool. If the fan fails or if the CPU gets old it may start to overheat and generate a particular kind of error called a kernel error. This is a common problem in chips that have been overclocked to operate at higher speeds than they are supposed to.
One remedy is to get a bigger better fan and install it on top of the CPU. Specialist cooling fans/heatsinks are available from www.computernerd.com or www.coolit.com
CPU problems can often be fixed by disabling the CPU internal cache in the BIOS. This will make the machine run more slowly, but it should also be more stable.
Power supply problems
With all the new construction going on around the country the steady supply of electricity has become disrupted. A power surge or spike can crash a computer as easily as a power cut.
If this has become a nuisance for you then consider buying a uninterrupted power supply (UPS). This will give you a clean power supply when there is electricity, and it will give you a few minutes to perform a controlled shutdown in case of a power cut.
It is a good investment if your data are critical, because a power cut will cause any unsaved data to be lost.
I hope now you will be able to rectify your problems. keep reading and learning.
posted by XERO . Anonymous Author
Thursday, 15 April 2010 by Lucky · 0
Wednesday, 14 April 2010
Eric S. Raymond throw some light on the most asked questions asked by amateurs and answers them in the most appropriate way. This is the ultimate hacking FAQ to go with if you are beggining to learn the art. This FAQ focuses on hacking ethics and right way to start and pursue your passion for it if you are really serious.
Interested ? Read on..
HACKING - Frequently Asked Questions
Q: Will you teach me how to hack?
Q: How can I get started, then?
Q: When do you have to start? Is it too late for me to learn?
Q: How long will it take me to learn to hack?
Q: Are Visual Basic or Delphi good languages to start with?
Q: Would you help me to crack a system, or teach me how to crack?
Q: I've been cracked. Will you help me fend off further attacks?
Q: I'm having problems with my Windows software. Will you help me?
Q: Where can I find some real hackers to talk with?
Q: Can you recommend useful books about hacking-related subjects?
Q: What language should I learn first?
Q: Do I need to hate and bash Microsoft?
Q: But won't open-source software leave programmers unable to make a living?
Q: How can I get started? Where can I get a free Unix?
Wednesday, 14 April 2010 by Lucky · 0
