Friday, 31 December 2010
Hi friends.. A very happy new year 2011 to all of you. My exams are over & I will be back to blogging soon, sorry for almost no updates. Perhaps I was just waiting in time to settle all the scene wars & post some new stuff. I have made some new friends, met some old ones & wish to continue our journey of knowledge with you, & just you folks only.

May this new year, you all be showered with the best almighty has to offer, & he shall empower you to fulfill your new year resolutions :D amen..
Rishabh Dangwal
Friday, 31 December 2010 by Lucky · 0
Sunday, 28 November 2010
Indeed: the basics!! Before I start out with something really technical, I thought to clear all the basics which are needed
I. Starting with Bits and bytes:
BIT - The smallest possible piece of data in computing can be either 0 or a 1. Put a bunch of bits together & tada..You will have a 'binary number system'
For e.g.
00000001 = 1 00000010 = 2 00000011 = 3 etc.
BYTE – A byte has 8 bits & can have a maximal value of 255 (0-255). We use the 'hexadecimal number system' for an easier reading of binary number system which is a 'base-16 system', while binary is a 'base-2 system'
- WORD –A word = 2 bytes put together or 16 bits & can have a maximal value of 0FFFFh (or 65535d).
- DOUBLE WORD –A double word = 2 words together or 32 bits & can have a max value = 0FFFFFFFF (or 4294967295d).
- KILOBYTE –1000 bytes?! Nah, it’s actually 1024 bytes.
- MEGABYTE –Again, not just 1 million bytes, but 1024*1024 or 1,048,578 bytes or 1024 KB.
II. A case of Registers:
Registers can be viewed as a placeholder in memory where we can put something; in simpler terms these are “special places” in your computer's memory where we can store data. View it as a little box, where we can put something: a name, a number, a sentence. Fact: Today’s WinTel (windows + Intel) CPU’s have 9 registers of 32 bit
Their names are:
EAX: Extended Accumulator Register EBX: Extended Base Register
ECX: Extended Counter Register EDX: Extended Data Register
EDI: Extended Destination Index ESI: Extended Source Index
EBP: Extended Base Pointer ESP: Extended Stack Pointer
EIP: Extended Instruction Pointer
Generally the size of the registers is 32bit (=4 bytes) & they can hold data from 0-FFFFFFFF (unsigned). In earlier days registers did what their name meant...Like ECX = Counter, but nowadays you can almost use any register you like for a counter or stuff (except counter functions, which I will be covering as we progress). There's one more thing you have to know about registers: although they are all 32bits large, some parts of them (16bit or even 8bit) can not be addressed directly as modern processors work n 32 bit protected mode.
The possibilities are:
32bit Register 16bit 8bit
EAX AX AH/AL
EBX BX BH/BL
ECX CX CH/CL
EDX DX DH/DL
ESI SI -----
EDI DI -----
EBP BP -----
ESP SP -----
EIP IP -----
To understand the above table lets consider a fictional value (my birthdate) as an example in hexadecimal & store it in register as –
30 Oct 1989
This can be written as: 30101989
Converting it in hexadecimal: 0x30101989
EAX = 30101989
Now as EAX (Extended AX) is 32 bit so it can store 30101989, therefore it consists of 2 AX registers which are of 16 bit each:
AX AX
3010 1989
& each AX is made of A H (Accumulator high) & A L (Accumulator Low) registers of value 8 bit each, taking AX = 3010 as example -
AH AL
30 10
Similarly for AX = 1989
AH AL
19 89
So we can say EAX is the name of the 32bit register, AX is the name of the "Low Word" (16bit) of EAX and AL/AH (8bit) are the “names” of the "Low Part" and “High Part” of AX. By the way if you have not forgot , 4 bytes is 1 DWORD, 2 bytes is 1 WORD.
Please Note: make sure you at least read the following about registers. It’s quite practical to know it although not that important. Also, the coming section may be a bit cryptic but will be explained in the followup tutorial.Since you are clear with the above, I guess we can make a distinction regarding size:
Byte-size registers: As the name says, these register are all exactly 1 byte (8 bits) in size & obviously it doesn’t means that the whole (32bit) register is fully loaded with data! Empty spaces in a register are just filled with zeroes.
AL and AH BL and BH
CL and CH DL and DH
Word-size registers: Are 1 word (= 2 bytes = 16 bits) in size. A word-sized register is constructed of 2 byte-sized registers. Again, we can Segment registers:their purpose:
- General purpose registers:
AX - ‘accumulator’: used to do mathematical operation & store strings.
BX - 'base': used in conjunction with the stack
CX - 'counter' used to count a value a number of times
DX - 'data': here the remainder of mathematical operations is stored
DI - 'destination index': i.e. a string will be copied to DI
SI - 'source index': i.e. a string will be copied from SI
- Index registers:
BP - 'base pointer' : points to a specified position on the stack
SP - 'stack pointer': points to a specified position on the stack
- Segment registers:
CS - 'code segment' : instructions an application has to execute
DS - 'data segment' : the data your application needs
ES - 'extra segment': points to the active extra-segment
SS - 'stack segment': here we'll find the stack
- Special: IP - 'instruction pointer': points to the next instruction. Just leave it alone
Double-word size registers: If you find an 'E' in front of a 16-bits register, it means that you are dealing with a 32-bits register. So, AX = 16-bits; EAX = the 32-bits version of EAX.
I believe I have covered registers this time, I will be covering Stack & instructions in my next article. Stay tuned & keep reversing
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Sunday, 28 November 2010 by Lucky · 0
Monday, 15 November 2010
Hi Friends..Sorry for long inactivity, I was busy in my personal projects & the mess which is called college life (i mean the good old exam time) :P . In the mean time a lot has happened in the security scene, which I believe you guys will be aware of if you are following My friends at Facebook, If not, I will be providing a brief review of latest happenings. First of all, November edition of Hacker5 is out & you can subscribe the wonderful magazine from here.

Secondly, NBC has proudly launched its venture of hacking which will be taught by some really good folks, No bullshit of basics, this is hard core. Coming down to the best news, Indishell is back :) . As signed by
[SiLeNtp0is0n], stRaNgEr , inX_rOot , NEO H4cK3R , DarkL00k , G00g!3 W@rr!0r , str1k3r, co0Lt04d , ATUL DWIVEDI , Jackh4xor , Th3 RDX & Lucky ;
Indishell aims to provide an intellectually stimulating environment where members can learn, communicate ideas and represent their concerns while supporting the advancement of the internet, technology and freedom.
I will be updating my blog as I get time, right now, I m kind of quite busy (writing an operating system :P as my final year project) , will catch you guys as soon as possible.
Keep learning.
like this post ? you can buy me a beer :)
Posted by XERO. ALL RIGHTS RESERVED
Monday, 15 November 2010 by Lucky · 2
Sunday, 24 October 2010
xtractr is a hybrid cloud application for indexing, searching, reporting, extracting and collaborating on pcaps. 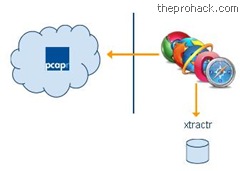
While xtractr can be used as a standalone application, it works best with Mu Studio to convert the problematic conversation into a stateful test case. The indices stays local to you on your network & you only access the application through the cloud. The analytics, searching, reporting and content slicing all happen between your browser and your xtractr instance. It also has a built-in web server, & supports more than one person analyzing the cloud at a time .You can have your team collaborate on it, label interesting flows, search, extract and report concurrently. You can even analyze different sets of packets on different ports on different tabs in browser.

You can check out the application here
like this post ? you can buy me a beer :)
Posted by XERO. ALL RIGHTS RESERVED
Sunday, 24 October 2010 by Lucky · 0
 hackers of India, in order to prevent cybercrime & attacks from foreign nations on our web servers. The campaign aims at projecting a positive image of hackers as heroes of computer revolution & not as a criminal, which I believe is a good thing for a country like India where hacking is still in a stage of infancy. The venture spans across internet using signature campaigns & print media using Hacker5 magazine. Unite Hackers is now a government recognized venture & the first of its own kind. In their own words -
hackers of India, in order to prevent cybercrime & attacks from foreign nations on our web servers. The campaign aims at projecting a positive image of hackers as heroes of computer revolution & not as a criminal, which I believe is a good thing for a country like India where hacking is still in a stage of infancy. The venture spans across internet using signature campaigns & print media using Hacker5 magazine. Unite Hackers is now a government recognized venture & the first of its own kind. In their own words -"I request you all to support this campaign to unite all hackers of India under one roof to protect our country and make it cyber crime free. All hackers are not Criminals, they are the Heroes of the Computer Revolution. Let us make this country cyber protected with this young think tank, 73% hackers of India are in the age group of 12 to 19, they don't have direction. Let us unite these think tanks and spread awareness.”The campaign is in its full swing, but as usual, there are people whose ideals differ from the above stated & they tried to defame Unite Hackers.
In Indian scene, there are prominent groups like Indian Cyber Army (ICA,the real one), Indishell , Indian Cyber Warriors/Andhra Hackers, HMG who are quite active. What I believe, success of project lies in the willpower to turn something into successful. Unite Hackers is a novel concept in India where hackers leave their field either due to career problems or due to lack of teams. The success of project will guarantee motivated folks who will be able to pursue their passion in computer security. Fellow bloggers Parul Khanna, Rahul Tyagi, Prateek Singla, Raghu Sharma & Amarjeet Singh are a part of this project.
If you want to support the project, leave your comments here.
cheers :)
by Lucky · 0
Monday, 18 October 2010
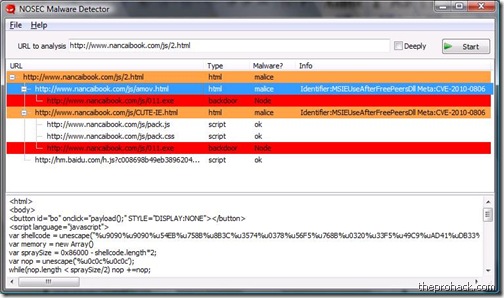
Nosec has introduced NSDECODER which is a automated website malware detection tools. It can be used to decode and
Functionality
- Automated analyze and detect website malware.
- Plenty of vulnerabilities.
- Log export support HTML and TXT format.
- Deeply analyze JavaScript.
Downloads
You can download NSDECODER one of these following links.
like this post ? you can buy me a beer :)
Posted by XERO. ALL RIGHTS RESERVED
Monday, 18 October 2010 by Lucky · 0
Sunday, 17 October 2010
Recently, i tried to have a paradigm shift of some sort, to move from ASM to web technologies, 
The results ? well, I found some vulnerabilities in some prominent sites which I am disclosing here..,the deal is that I tried to contact the vendors (more on this later) to notify them of vulns. Remember hackable government & educational websites, consider this as the spiritual follow-up of the article.
Disclaimer
I HAVE NOT HACKED ANY OF THE SITES AND THEIR DATABASES IN ANY WAY,JUST TESTED WEBSITES FOR VULNERABILITIES. I TESTED THEM AND FOUND ERRORS WHICH MAY/MAY NOT BE DISCLOSED HERE AND IN NO WAY ANY ONE CAN SUE ME FOR THIS AS I DID AND MEANT NO HARM TO THE DATA OF CONCERNED ORGANIZATIONS.
BY READING THIS ARTICLE YOU AGREE WITH THE DISCLAIMER.
IF YOU AGREE WITH THIS AGREEMENT,CONTINUE READING ELSE IMMEDIATELY LEAVE THIS WEBSITE.
Here we go, it all started with www.in.com [ ALEXA RANK 298 ] which had a simple XSS vulnerability to display cookies , inject code & God knows what else, I tried to contact the technical team in vain, then contacted them via a simple feedback form. Waiting for their response as of now..I moved on then. Please note that I have censored all the URLs & script details so as to protect attack originating after this article :P

I never liked Rediff [ ALEXA RANK 128 ] & their services..too much ads to digest for me, again, it was easy to inject .

dl4all.com [ ALEXA RANK 1517 ] was no exception, a simple search & thats all.

shaadi.com [ ALEXA RANK 935 ] the premium matrimonial portal of India has XSS flaws..


A leading social networking website Itimes.com [ ALEXA RANK 6024 ] was no better & a nobrainer.

Indiatimes.com [ ALEXA RANK 168 ] anyone ?

enough..as expected, I tried to contact all the support staff before releasing this article. My point ? what happens when there is no competent technical staff to handle the issue (I am looking at you AXISBANK !) have a look at it

great..now that's what we wanted..more flaws in “secure” websites which pledge for our privacy. For the record, XSS flaws are independent of encryption & the so called layman lock mechanisms as the application behavior remains the same. I tried to contact authorities at AXIS bank but they were asking for my bank account number, to contact nodal officer, to contact xyzabc blah blah..but no support / tech staff.
Lets have a look at the alexa rank of the above websites -
www.rediff.com - 128
www.In.com - 298
www.Indiatimes.com - 168
www.shaadi.com – 935
www.dl4all.com – 1517
www.axisbank.com - 2330
www.itimes.com – 6024
again, the above sites are the head honchos of social networking, downloads, have a lot of data in their hands & are vulnerable to XSS. Why they still have no technical feedback team is beyond my belief. Except itimes, i wasn't able to find a bug reporting facility in any of the sites mentioned above. Now that's pure genius ! Just what were they thinking ?!! Cant they learn from some good examples ?
what i am doing ? to quote Rsnake
“ How many compromises of data security, that you are aware of, have been disclosed to the public as a percentage? “
ditto here..the websites are not safe, & so their claims. It took me about 30 minutes to write this post including the time to try XSS on the websites, ( excluding the email contact with the authorities where possible ). XSS/CSRF is the modern nightmare of security for any website today, prominent websites are constantly under attack & the recent cases which i have heard as of now, lot of bank websites were targets of CSRF based attacks, phishing & XSS. Imagine what a skillful attacker can do with a lot of time & patience (& a reason perhaps).
pray & spray..& trust no one.
like this post ? you can buy me a beer :)
Posted by XERO. ALL RIGHTS RESERVED
Sunday, 17 October 2010 by Lucky · 0
Thursday, 14 October 2010
Sorry for a late update folks, I m just back from SRM CEM lucknow, where I was invited to deliver a seminar on Reverse Engineering & application cracking using custom code. Lucknow was a blast, the students there were very cooperative & I was accompanied by my best friend Prateek Singla, fellow teammates & hackers Parul Khanna, Rahul Tyagi & Mr Ajay Anand. You can see that we really had a blast there :D

The Team

The Lecture

The Aftermath
Plus,recently I was interviewed by the folks at hacker5 magazine, which is the first hacking magazine of India.I m publishing excerpts of the interview here.
Hacker5: About you ?
Me : I am a peaceful little ghost & have a passion for computer security. Please note I am not a hacker. I m more of a computer security researcher.
Hacker5: Your Rig ?
Me : Fedora 13 x86 on Intel dual core 1 GB ram. A modest machine, but customized to anything :) Want to move on to SPARC architecture for a change.
Hacker5: Your Life style ?
Me : My Lifestyle ? Waking up early in the morning to exercise, tone my body,mixing up with people, going college. The real part starts after dinner, logging into irc to roam free as a bird in freenode, watching cracktros, reading about virii at netlux heavens, reading usenet newsgroups, going through with retro files , ASMX86 & C program crunching, emulators,& reading phrack magazine & ezines through the night,..only to wake up in the morning to know that you have been late to college..when I m not messing with computers, I m into classic Halo & videogame reviews. AVGN,XKCD,Theoatmeal are a favorite.
Hacker5: How did you get into hacking ?
Me : It all started as when I didnt get into medical line..then a revelation occurred , My friend Prateek inspired me into this & i went with basic windows, learning the OS, knowing its structure, mingled with programming in C/C++. partly, I got encouragement from my lecturers who actively supported my passion. Later on I drifted to ASM & Linux (I am still getting better) & was inspired by emulators by El Semi & the Kawaks team. Debugging into ROM files, hacking N64 data roms, ppf patching in playstation & studying how programs worked in low level..that was all my life in class 12 to Btech 2nd year. I hated databases by instinct & never got good at them, but later on when i fully switched to linux (courtesy of Raghu), I came to know about the intricacies of MySQL & open source platforms..& was hooked to it till Oracle purchased SUN.
Now I m into ASM again.
Hacker5: How you have started your organization
Me : Organization ? nah..call it a fanbase, a movement. I started PROHACK with only one thing in mind, to share what I knew..the start was tough but later on, It gained momentum.
Hacker5: Family support ?
Me : Ah well..initially my family was not that supportive for my passion, but as time progressed, they cooperated & backed me up. My father is my backbone & the pillar of strength for me. I thank God for making me who i am.
Hacker5: SWISS bank hacking & politicians...provide few scandals.. ?
Me : Not interested. Call me an anti politicist
Hacker5: Hackers resources for both white hat & black hat
Me : PHRACK magazine, ezines , IRC, Usenet, newsgroups, forums,manuals of devices & programs..its all there, you only need to see through it.
Hacker5: USENET concept as only 7% data is available on Google
Me : USENET has been into scene even before Internet, & its something to experience. However, even today, its in infancy (less than 20 groups in USENET from India), you can say 90% of people don't get to know about it. internet as we see is the public network, the scary truth is that the major networks are always hidden & they are quite prominent behind the scenes.
Hacker5: SUNNY VAGEHALA truth.. who hacked Orkut
Me : Those who cant code are not hackers.
Packet monkeys?
YES.
Script kiddies?
YES .
Hackers ?
NO! .
Next question please.
Hacker5: Your views on Ethical Hacking
Me : I have problems with some folks who call them ethical hackers. There is nothing called as Ethical hacker, Hacking is an art & there is nothing unethical in doing Hacking. Ethical hacking is analogous to saying Ethical Rapist. however, Hacking is the passion to pursue anything with deepest dedication, its all about knowing computers as they are & beyond. That's why..its rightly said, there is nothing called as an Ethical Hacker..Hacking is an art & you need no ethics to pursue it. & for God's sake no body is a hacker till he can code, & till he can code with absolute efficiency...till then he might be a security liking guy, an admin, a packet monkey..but not a hacker.
Hacker5: Views on Open Source
Me : An absolute necessity nowadays..its the key to connect with developers all over the world. .its about freedom..I mean what's the point in using a tool designed by other, unless its open source ? a closed source tool is as dangerous as a virus, we just don't know what is behind its hood & what it may cause to anonymity & efficiency of a successful xpl0it. why not to get a low level knowledge of packets & protocols & write off a code to sniff it out, that may take time, but that is foolproof...it will make a good programmer out of you & you will be able to customize it to your limits
Hacker5: The Hacking Underground ?
Me : I m more of a coder...I was more interested in international scene, for the security scene in India is in the state of infancy. The scene is degenerating & its better to have a look at it while its still there <hint:IRC/USENET>. India's team technotrojans (team t3) & their disappearance from the web..I wonder where are they now,didn't knew them personally, but they spearheaded the scene at one time.
Hacker5: Views on Pakistan China Cyber attacks
Me : Ah well..as far as Indo-Pak cyber war is concerned, what i have seen is that its nothing more than defacing websites for pure revenge. Nothing more,nothing less. I highly respect Saqib Akhtar (from PCSX2 dev team) as he has been my hero for last 2 years as a driving force to get better at low level code. I believe the war is futile..why not to get better & share code..amen
Hacker5: Your Heroes ?
Me : The_ut, Richard Stallman, Linus Torvalds, Eric S Raymond, Alan Cox,Fyodor, FX of Phenoelit, Wesley McGrew, geohot, Saqib & me :)
Hacker5: Dream ?
Me : To be a speaker at Defcon, be a legend like the_ut, get money, get rich :D
Hacker5: People you wish to thank
Me : My father, Prateek, Martin, Silverbullet, RS3V3, Neha, Param & Saloni. Thanks for making me who I am today :)
Hacker5: Contact
Me : You can find me roaming in the IRC's, surfing wikipedia & ezines & dorkly/XKCD/Phrack/textarchives/preterhuman & studying snippets. Else while you can find me inside HOD's office :D or roaming into corridors of college snooping into netgears .
You can get the hacker5 magazine from here :)
will be updating you guys soon :) A very special thanks to Vaidehi Mam & Amarjit Sir for giving me a platform. greetz fly to folks at SRM.
like this post ? you can buy me a beer :)
Posted by XERO. ALL RIGHTS RESERVED
Thursday, 14 October 2010 by Lucky · 0
Sunday, 3 October 2010
Its been some time since I have written a reverse engineering tutorial, & I thought it would be good to cover one at the
Disclaimer – By Reading this tutorial You agree that this tutorial is intended for educational purposes only and the author can not be held liable for any kind of damages done whatsoever to your machine, or damages caused by some other,creative application of this tutorial.
In any case you disagree with the above statement,stop here.
Requirements
- A-one Video to Audio convertor (Download from yaomingsoft.com)
- OllyDBG
- Time & Patience
Download & install A-one Video to Audio convertor. Now as you can see, its a trial version & once you try to register it, it gives an error <obviously>, & we need to find ways against it.

Now, to being with, fire up OllyDBG & load the A-one Video to Audio convertor EXE file in it.

Now, right click on
CPU window -> Search for -> All Referenced Text Strings

& in Text string window, right click -> paste the "Registration code is error" string (which pops when you input wrong serial) After you find it, double click it & navigate to the memory address.

Now, once you have reached the intended memory address, you can navigate a bit up to see the "register successful" string.

Navigating a bit above will get a simple logic which calls a specific function, & then the function returns a result which is compared to EAX
CMP EAX,1
& then jumps to 407A0F
JNZ SHORT 00407A0F
which is the "register failed" condition.
The whole scenario means that if value of EAX is anything less than or grater than one, the program will be a trial version & will not accept any invalid serial key.
Now, you can put a break point above the function call by pressing F2 & run the program, & enter the serial, the program will break & we can then navigate inside the function by pressing F7
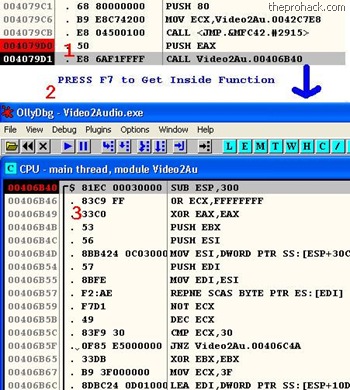
You will get into function code. Add the breakpoint there by pressing F2 & restart the program again by pressing Ctrl + F9
Run it again & you will find that it will break it at 00406B40 (where you put the last breakpoint)
now, we will execute code step by step by pressing F8, once we go a bit down, we find
JNZ Video2Au.00406C4A
which jumps below to
POP EDI
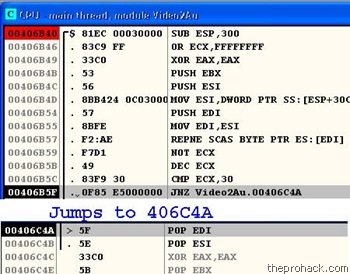
& further we find that the value of EAX is XORed to 0.

so in order to insert a precise value into EAX, we will modify by double clicking
XOR EAX,EAX
& changing it to
MOV AL,1

which will set the accumulator's value to 1 because
EAX - 32 Bit reg <extended>
AX - 16 Bit reg pair
AH / AL - 8 Bit regs
where AL will represent the lower value, & setting it to one will set the accumulator to a precise value of 1, hence setting value of EAX to 1,which will lead to program being registered :)
now once you have done it, right click the code,
copy to executable-> selection.
In the coming window, right click again, save the file & you have a cracked working version of the software, paste it in program files directory & insert any serial.
it will work :D

I hope you liked it :)
like this post ? you can buy me a beer :)
Sunday, 3 October 2010 by Lucky · 1
Thursday, 30 September 2010
Newsmakers Broadcasting & Communication Pvt. Ltd is coming up with a niche magazine based on the cyber happenings which is the need of today in the IT industry which is touted as the first Hackers magazine of India, & I along with a lot of good people out there like Parul Khanna , Rahul Tyagi will be publishing a lot of articles in it :) . The magazine ‘Hacker5' would be launched on 7th October, 2010 at Chandigarh Press Club, Sector 27, Chandigarh, Punjab.

The event will be organized with the presence of high profiled dignitaries from Punjab, Haryana and New Delhi. Shri Prakash Singh Badal, Chief Minister of Punjab, Shri Bhupender Singh Hooda, Chief Minister of Haryana are some to name.
Kindly grace the event with you presence. This is an OPEN event and all of your are Invited. If you face any problem, you can contact @ +91-9953926905
Cheers :D
like this post ? you can buy me a beer :)
Thursday, 30 September 2010 by Lucky · 0
Wednesday, 29 September 2010
A Demolishing analysis of Ankit Fadia's Ethical Hacking Seminar - Overrated, Overhyped & Pure waste of Time

He was worse.
No offense to Mr Fadia, but actually I was quite saddened by some of the questions which he asked-
How many of you use Google as a search engine ?
(Almost all of hands raised)
He Proclaimed - STOP USING THEM !!
How many of you use email services like Gmail, yahoo?
(A lot of hands raised)
He Exclaimed - STOP USING THEM !!
How many of you use internet ?And behind the above "Stop Using Them!!" there were some cheesy reasons of privacy invasion & record tacking. I wondered why he was not educating about how to use services like Scroogle/TOR/SOCKS for safe surfing (albeit nothing is safe, but still, they provide a greater degree of anonymity). Then..it all begin.
(again..some of hands raised)
STOP USING THEM !!

Part 1 - Screwing the Proxies
Then the hacking prodigy demonstrated his magical wits by recommending Russian proxy servers cuz "they were maintained by criminals" & "they kept no logs" .
F**INGBULLSHIT !!
Why the hell ! We can never trust a proxy if it keeps logs or not, that's why we always use SOCKS & proxy chaining to get the work done, even when I start something casual, i chain 10 proxies using a TOR network to get the work done, & that guy was recommending anonymizer.com & anonymizer.ru . And we shall trust Russian proxy cuz its maintained by criminals ? what an oxymoron ! His ace in hole in the proxy demo was the Princeton university proxy list where he claimed that to black all of the proxies it will need 413 individual tries ! A friend of mine asked -
"Well Mr Fadia, what if you block the Princeton university site ?"Pure F**king Genius !
pat came the nervous reply
" Appoint a junior of yours to go into local cybercafé to get the list, Xerox it and distribute in college"
He went on to use SPYPIG to get IP of any person using an image. but he didn't get on the point that what if a person has disabled image viewing on email. Anyways..it all ended with a lot of questions which he dodged by saying that there will be a query session in the end. Ah well..
Part 2 - the infamous NETBUS DEMO
I patiently waited to ask him some questions regarding IP evasion & anonymity but he started to demo NETBUS Trojan, without any logic he went on to demonstrate how he can open his CD/DVD drive on his DELL Studio 14" (by installing a Trojan server on his own laptop & executing commands on local loopback & he didn't explained it, that's why its in f**king brackets !) . I asked him, on getting chance from my trusted roommates & event co-ordinators Sumit Dimri & Varun Kumar Singh & asked him 2 simple questions (Of course I already knew the answers) -
- What happens if a person is behind a NATBOX/Router/Firewall, then there is no use of getting IP, it might not be forwarded at all. What then ?
- Trojans are invalid against Linux. What can you do to break into Linux Security ?

Again..Pure F**king Genius !
From that point i got the point that he has no point :D
We moved on to the Steganography / Final session then.
Part 3 - the Steganography / Final session
The steganography session was started by exclaiming that he was contacted by FBI on 9/11 attacks (which i already knew as a matter of fact is fake courtesy of Attrition.Org & various LUG's out there) & they used images of sexy women to transmit data into them. He used a tool to hide text data into image & reverse it, nothing special, if you have been a reader of my blog I guess you probably know that Nettools allow you to do that. Then he demonstrated Bluetooth hacking by using bluesnarf (just a scan) & website hacking using SQL injection (again..nothing special) with no logical explanation of how the injection worked. The session ended by "Roadside Sign hacking" in which he displayed pics on projector of hacked road signs by hackers at USA, Australia & other countries.
He then begin to advertise Dell laptops & the highly prestigious (READ: BELOW AVERAGE) AFCEH course conducted at Reliance Webworld. Then he ran away cuz he was running short of time & no Query Session was conducted.
Aftermath : Pure F**king Genius !
I guess you realize what I felt for the whole seminar & the whole Ankit Fraudia oops.. Fadia hype..
My Feedback form read -
Name : Rishabh Dangwal
Qualification: Btech
Branch : CSE
Remarks : Ankit Fadia is Overrated..Overhyped & pure waste of time. If you are bored, do come to Fadia for a few laughs. Peace.
EOF
Posted by XERO. ALL RIGHTS RESERVED.Source
Wednesday, 29 September 2010 by Lucky · 2
Monday, 27 September 2010
Yep..I perfectly know why you are here..You wish to recharge your phone for free, probably just for funs sake or just 
What you need ?
- Email ID
- Cellphone
- A registered number & sim
- Patience

How to Do it ?
open your email account by entering your username & password, & drop an email to your telecom service provider -
Dear Sir/Madam/Whatever
I would like to bring to your attention that I have been trying to learn how to recharge my cellphone account for free by searching on the internet but in vain. I am very hopeful that I would be able to find an authentic way to top up my account for free one day.
I have this funny feeling that you organization is a silly company who will allow me do unlimited top ups on my account.
Anyhow, I am a good guy and would resort to extreme ways,rather I humbly request you to provide me the recharge code of atleast 5000 INR.
Thanks for your cooperation.
Regards
Your biggest Fan :)
9XXXXXXXXX
That was easy…isn't it ?
Just Kidding folks..I was having some harmless fun at your expense.
How actually you can Recharge your cellphone / top up for free ?
Open Notepad & type
I am fooling around with this article thats making a fool of me :)
WTF ?
Still reading ? Ah well..Sorry once again guys..Actually, what I was thinking that upto this point, any self respecting noob might have closed the browser window and moved on to a different page.
I wrote this article as I was inspired by the fake recharge/top up code calculator programs scattered all over the internet. Especially this one in which a hex editor is provided to the unassuming audience in order to increase blog SEO.Great..now on to the actual topic, you CAN have free calls, unlimited SMS & every other facility for your cellphone. You need to have (Cheap method) -
- Asterisk SwitchVOX
- SIP connection (Session Initiation Protocol)
- Knowledge of Linux + Servers
- Lots of time
OR
You can have
- Lots of Money
- MINSAT (Mobile Intelligent Network Service Administration Tool)
- Internet connection
- Lots of knowledge + time (again!!)
Due to some constant bullying by legal guys, I cant really publish the full method to go with recharges, but atleast I can give cues :D
The Intelligent will find the way..
like this post ? you can buy me a beer :)
Monday, 27 September 2010 by Lucky · 0
Tuesday, 21 September 2010
WTF ? DMC5 ? at TGS 2010 ? released on 15 september, I got hold on the DMC 5 traileror you can say DmC trailer.For those who dont know what Devil May Cry is, go to the corner & wear the dunce cap ! Devil May Cry is the hack & slash action game series by Capcom featuring one of the most intricate fighting system & coolest protagonist Dante, its the game against which other Hack & slash games are measured!! The new DmC is said to be a reboot of the series. REBOOT ?!! Ah well.. I will come to the point later, lets first have a look at the trailer.
Man..what were they thinking ? Where the hell is all badass Dante ? The silver haired demon slayer has been dumped for this skinny juvenile ? & a Reboot ? What happened to Nero ? What about the legend of Sparda ? Man..even Hideki Kamiya, the creator of DmC commented

“I miss him, too…” and later added “I’ve been sad since Dante left me.”In a later tweet when a fan asked the question:
“DmC by Ninja Theory? Do you think they will evolve the action game from your Bayonetta standard?”,Kamiya-san simply said:
“whatever”See ? Dear Folks at Ninja Theory..Better be the game badass, else while this new Dante might prove your last stand.
Well..looking at the trailer, some things pass my mind -
- New Dante looks like ass!
- It might not be a reboot at all (.0001% chance) & this might be the story of an abandoned Dante struggling with his goddamn teenage, & later at the end of game, the prologue of Devil May Cry 3 begins.
- The visuals are improved, especially the blur & sonic effects.
- The new weapon is ass! Except the Sword..I dont like the Daggertail like thing Dante holds..The Dante I knew like to take things Up close & PERSONAL !.
Tuesday, 21 September 2010 by Lucky · 0
Tuesday, 14 September 2010
Great…just came to know from “El Reg” how an obsolete parameter in a program separate from OS can wreak havoc. 
“The bug is is pretty bizarre,It's not a standard vulnerability in the sense that a feature was implemented poorly. It was more kind of a leftover development piece that was left in production. It's probably an oversight.”
How the punk pwned ?
Schemes like DEP , or data execution prevention prevents any code from being executed & ASLR, or address space layout randomization, loads code into locations that an attacker cant predict there by securing parameter to some extent in Windows architecture. “_Marshaled_pUnk” however creates an object pointer equivalent that an attacker can use to load & malicious code into computer memory. In a witty maneuver, Santamarta used a technique called return oriented programming also known as ROP to load code by loading WindowsLiveLogin.dll into memory & reordered the commands in a way that allowed him to gain control of the testbed. Using the Microsoft DLL not only allowed him to know where in memory it would load, it also allowed him to get the code executed.
What next ?
Santamarta confirmed the exploit on the XP, Vista, and 7 versions of Windows. He also said that the parameter existed in QuickTime version dating back to 2001, when it could be used to draw contents into an existing window instead of creating a new one. The functionality was eventually removed from newer versions but the line lived on. Combined with an unrandomized DLL like the one for Windows Live, it represents a serious threat to end users. The flaw has demonstrated that the threat comes from the programs that fail to use ASLR & DEP protections, surprisingly as reviewed by Secunia ,a large number of popular applications — including Quicktime, Foxit Reader, Google Picasa, OpenOffice.org, RealPlayer, and VLC Player — neglect to use one or the other.
Till then..wait for Apple to release a patch for the 9 year old Punk.
like this post ? you can buy me a beer :)
Tuesday, 14 September 2010 by Lucky · 0
Monday, 13 September 2010
Packet-o-matic is a modular real time packet processor under the GPL license. It reads the packet from an input module, match the packet using rules and connection tracking information and then send it to a target module. The modular nature of packet-o-matic allows it to work for any protocol as long as its corresponding module is found. The built in management console allows you to telnet in packet-o-matic and change the configuration in real time. Main features of Packet-o-matic are :
- connection tracking currently for ipv4, ipv6, tcp, udp, rtp
- ip reassembly, tcp reordering
- match the complete protocols encapsulation i.e. "ethernet->ipv6->ipv4->udp->rtp"
- process all the packets in real time to provide the desired output
What it can do ?
- save all the VoIP calls going on an interface in separate files in real time
- reinject packets destined to a specific ip and port on another interface or save them in a file
- dump each file of all the http connections in separate files on the disk
- show the important info and an hexadecimal dump of each packet while doing the above three at the same time
- lots of other stuff which would be too long to list here
Operating System Supported : Linux
like this post ? you can buy me a beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Monday, 13 September 2010 by Lucky · 0
Saturday, 11 September 2010
ObiWaN is the brainchild of Phenoelit, a german hacker group headed by elite hacker FX which is written to carry out brute force security testing on Webservers. The goal of ObiWaN is a brute force authentication attack against Webserver with authentication requests - and in fact to break in insecure accounts. As the official documentation says -
ObiWan is written to check Webserver. The idea behind this is: Webserver with simple challenge-response authentication mechanism mostly have no switches to set up intruder lockout or delay timings for wrong passwords. In fact this is the point to start from. Every user with a HTTP connection to a host with basic authentication can try username-password combinations as long as he/she like it.
Like other programs for UNIX system passwords (crack) or NT passwords (l0phtcrack) ObiWaN uses wordlists and alternations of numeric or alpha-numeric characters as possible passwords. Since Webservers allow unlimited requests it is a question of time and bandwith to break in a server system.

ObiWaN manipulates a weakness in HTTP protocol, which as explained by Phenoelit itself is that nearly all servers allow unlimited username/password tries for a user & it literally becomes a question of time and bandwith to break in a server. After you break-in,you are the alpha & the omega of server..
enjoy :)
like this post ? you can buy me a beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Saturday, 11 September 2010 by Lucky · 0
Wednesday, 8 September 2010
Securitytube
watch-learn-contribute..A site packed with lots of security related videos,resources & up to date news.
Offensive Security
Need I say more ? The creators of the reknowned security distro Backtrack maintain one of the best happening forums on security. The link above relates to backtrack tutorials & forums, explore & learn..as always,the quieter you become, the better you are able to hear.
SmashTheStack
Like Wargames ? Smash the stack is your portal for the ultimate wargames which will escalate your level from nothing to something..pay attention,play well & learn.
PaulDotCom
One of my favorite security podcasts,the website provides insightful papers,presentations & discusses on hot security topics.
Tuts 4 You
Reverse engineering anyone ? Tuts4You is a community for researchers and reverse engineers interested in the field of Reverse Code Engineering (RCE). Great tuts..Great resources..
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
Wednesday, 8 September 2010 by Lucky · 0
( PS: Folks..if you think you are too dumb to do
that, there exists an automated "burn-the-cd-boot-&-forget-solution"
called KONBOOT which can reset Linux passwords if you care.. :D choose your pick )
I actually rebooted the system & once I reached grub,selected the kernel, I pressed "e".I proceeded to 2nd line of configuration & pressed "e" again.
kernel /boot/vmlinuz-2.6.34.6-47.fc13.i686 roObviously, I edited the file by pressing "e" again & modifying it by typing "single" for invoking single user mode in Linux.
kernel /boot/vmlinuz-2.6.34.6-47.fc13.i686 ro singlePress "b" key to boot. Afterwards, you are given a prompt, please enter "passwd" command to reset root password.
After that, login as root & then proceed to move to /etc/shadow
[root@zion XERO]# cd /etc& check the entry for root,it should look similar to this
[root@zion etc]# vi shadow
root:$6$McKhE96JGhl$uIfjBcMrrrL2x8aJ17mATex8WNXVMvZXrsfqoOL.
CinR9W2C8VXVyt4W2yt4eAJ0tgNPU2Kftr1f/lcvDG.:14859:0:99999:7::1:
you can see there is a "1" in last entry which sets the root account to expire. remove it such that it becomes
root:$6$McKhE96JGhl$uIfjBcMrrrL2x8aJ17mATex8WNXVMvZXrsfqoOL.
CinR9W2C8VXVyt4W2yt4eAJ0tgNPU2Kftr1f/lcvDG.:14859:0:99999:7:::
Once done, save the file & exit by pressing :wq! in vi. After that, boot into graphical mode by typing
[root@zion XERO]# init 5login with your password."root" problem solved :) After wards..i found out that my hostname was changed..so, here are three easy ways to change your hostname on your will.
Way 1
open console, & type
[root@zion XERO]# hostnamenow you can reset hostname (for the given session) by typing -
NETWORKING=yes
HOSTNAME=hosty.test.com
[root@zion XERO]# hostname myhostname.mysite.comwhere myhostname.mysite.com is your new hostname.
WAY 2
The second way deals with editing a file known as "network" located in /etc/sysconfig/network, navigate to it
[root@zion XERO]# cd /etc/sysconfig/check the value of hostname in it
[root@zion sysconfig]# cat networktime to change it, go to vi & edit it.
NETWORKING=yes
HOSTNAME=hosty.test.com
[root@zion sysconfig]# vi networksaved the file..reboot & its done :)
NETWORKING=yes
HOSTNAME=myhost.testsite.com
~
~
~
:wq!
WAY 3
The third way deals with "sysctl" command, which can be used to change the variable kernel.hostname. Start by checking its current value by typing
[root@station3 sysconfig]# sysctl kernel.hostnameand to change it, enter
kernel.hostname = hosty.test.com
[root@station3 sysconfig]# sysctl kernel.hostname=MYHOST.TESTSITE.COM
where MYHOST.TESTSITE.COM is your new hostname. All of this was scripted,tested in FEDORA 13 (2.6.34.6-47.fc13.i686) & written using Scrib Fire
.
I hope it was interesting :)
Like This post ? You can buy me a Beer :)
Posted by XERO. ALL RIGHTS RESERVED.
by Lucky · 0

